We can sniff all traffic that is happening on our Android phone. The idea is by connecting our phone to a proxy that acts as MITM or Middleman. Same as Pi-hole able to showing all log DNS queries, Burp can be acting as proxy software to capture all traffic that comes to it.
Here is how it works from a high-level. Our phone connects to the internet as usual via the router. To monitor the traffic, we shall route our request to a single place, called a proxy server. This proxy will capture and have the ability to intercept the traffic and sending it to the internet. The response from the request is also going into the same channel flow.
Android Phone (Use Proxy’s Cert) —> Proxy —> Internet
How to ensure this solution works for HTTPS, which encrypted with certification? To make this works, we need to inject our certification into the device and make it trusted (There will be step for that). If our own certification acknowledged by the device, then we can decrypt the traffic from the server that issued the certification.
In this full guide on how to capture the traffic network, I am using a local wifi connection with Windows 10. There no significant difference when setting up this solution in Ubuntu 20.04 or Windows 10. Also, ensure your Android phone have access to the same router as your Laptop, where both IP can communicate under same network.
Attention, this step only works to capture all traffic from a mobile browser in Android that using HTTP and HTTPS as communication. This approach may not works for mostly app since they use SSL Pinning. I will cover the solution in next article. Also, you don’t need to root your Android phone to monitor the traffic.
Here are the guideline
1. Install Burp Suite Community Edition
Go to Burp Suite Free version download page and install it into your Windows 10 or Ubuntu.
2. Setup Burp Proxy on your Computer
Open the Burp Suite and click Next until the main page. Select Proxy and go to the options. Click Edit on 127.0.0.1 and change it into your IP address from Wifi. Go back to Intercept page and click off as now.
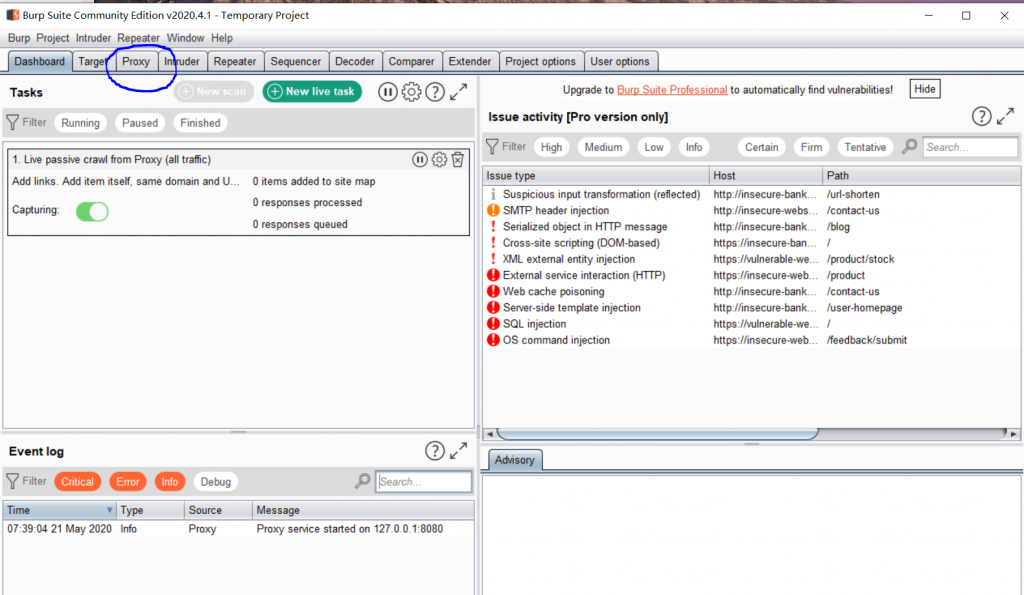
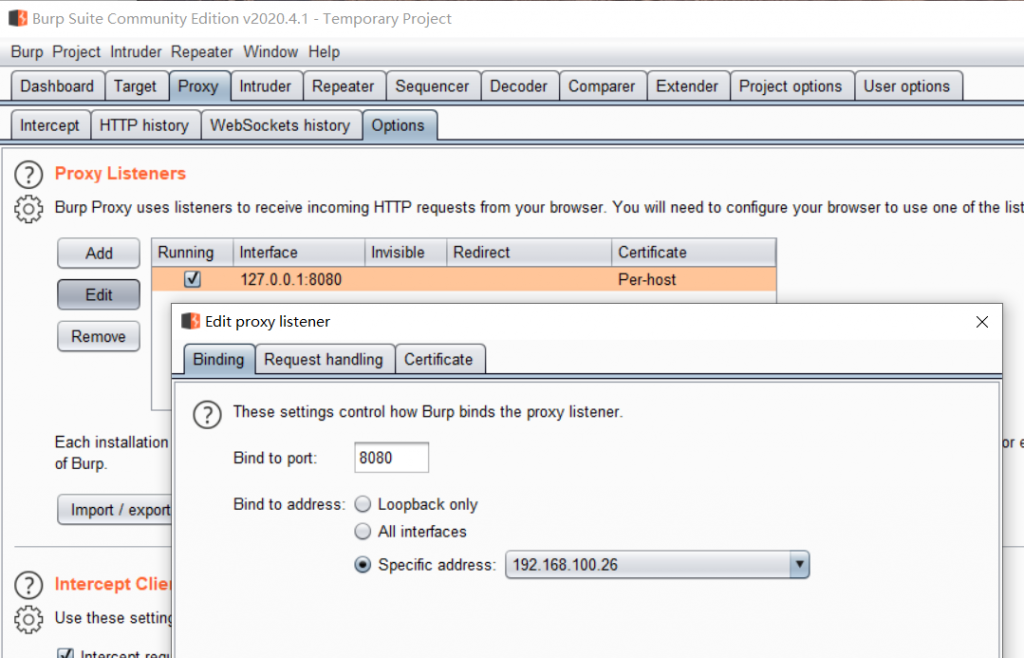
To test if the Proxy server is already running, please visit your IP:8080, and you should see the webpage with “CA Certificate” button on the top right. That is an important link because you need to download the certification from it.
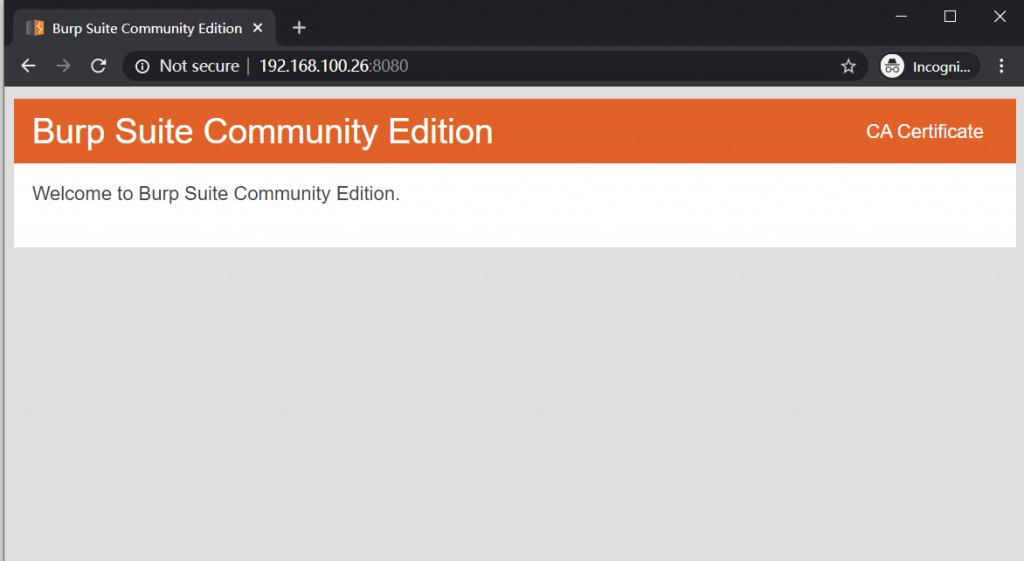
3. Make BURP’s certificate trusted by your Android device (non-root)
Go to your Android’s browser and open Burp IP:8000. Click on “CA Certificate” and Download it.
4. Install CA Certificate in Android
Next, go to files and move this certificate into home path “/Internal Storage”. Rename the extension “cacert.der” into “cacert.cer” to make it visible from Android certificate installation.
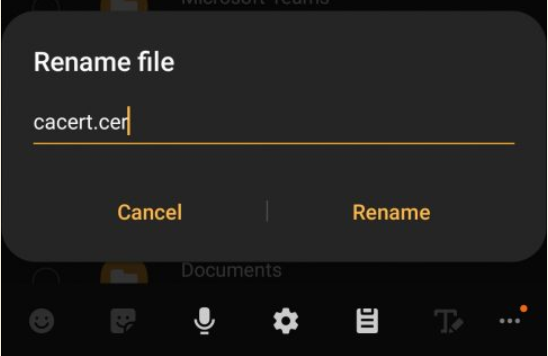
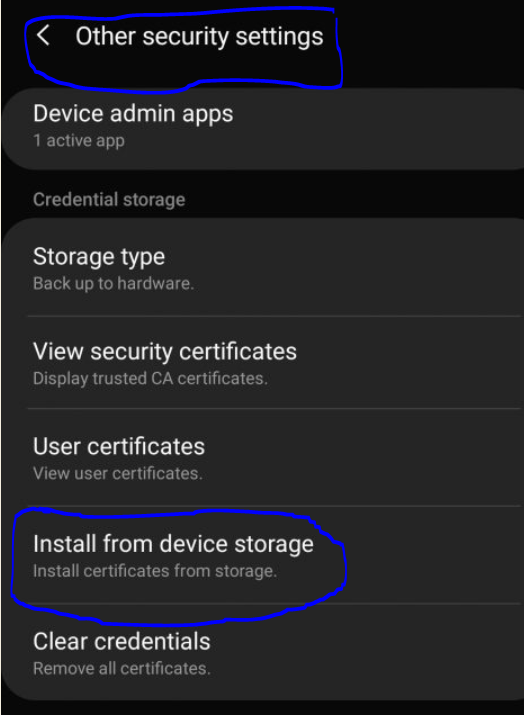
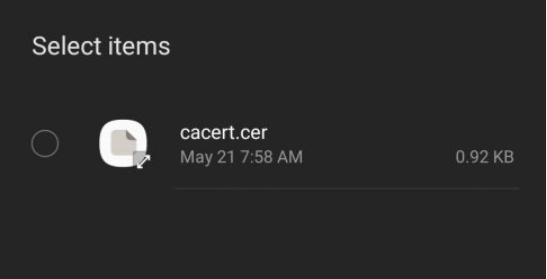
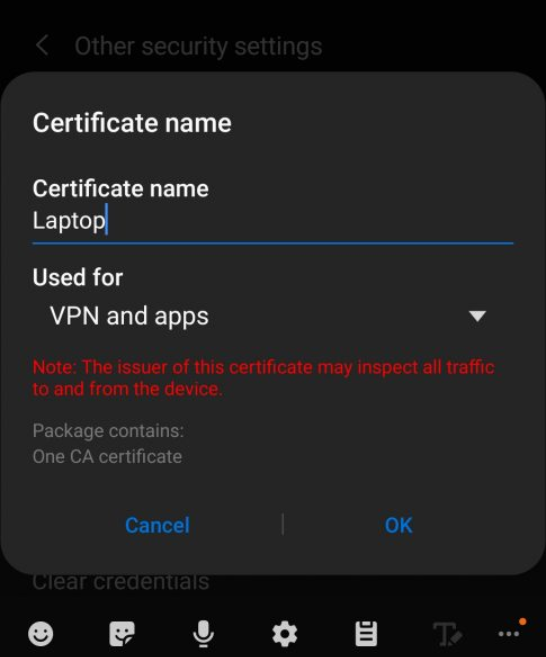
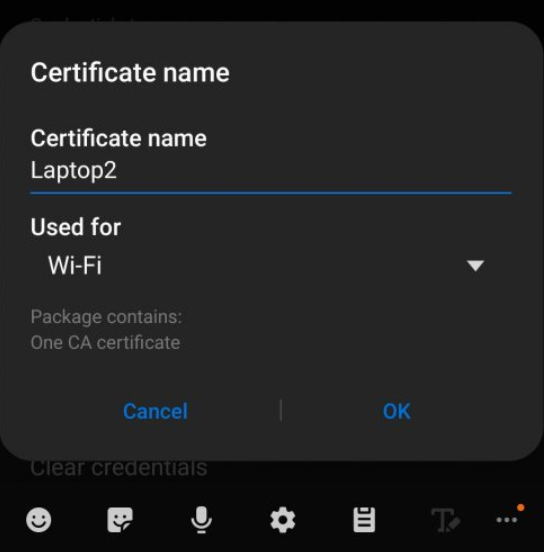
Go to “Other security settings” settings, click on “Install from device storage”. Select the cer file and setup it for both “Wifi” and “VPN and Apps” (we gonna use this in next article).
5. Configure your Android Wifi connection
The last step, go to your wifi settings and change the configuration to use proxy as your computer/laptop IP address where Burp Suite running. eg: IP:8080.
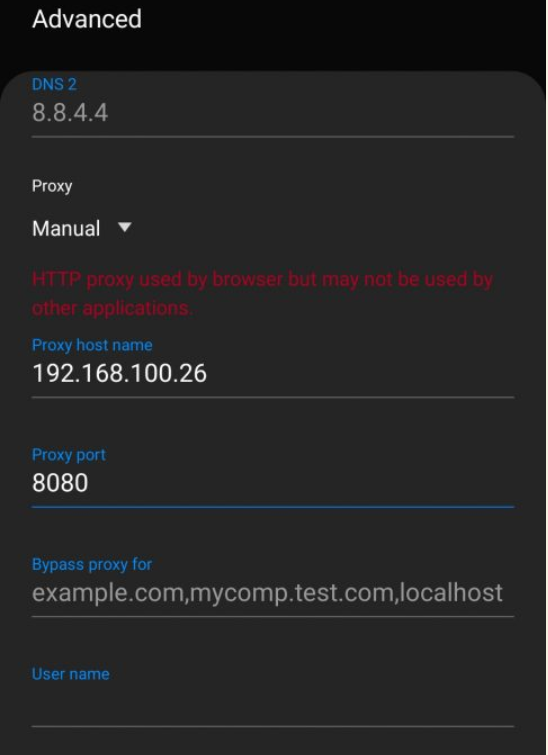
6. Test Monitor Traffic in your Android
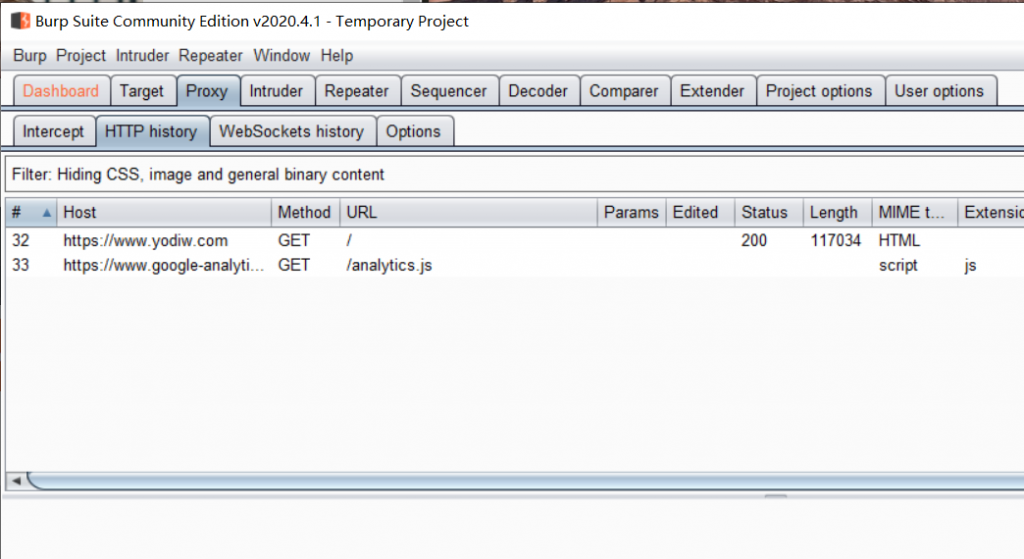
Go to your browser and open this page “https://yodiw.com” and you should able to see the traffic in Burp Suite
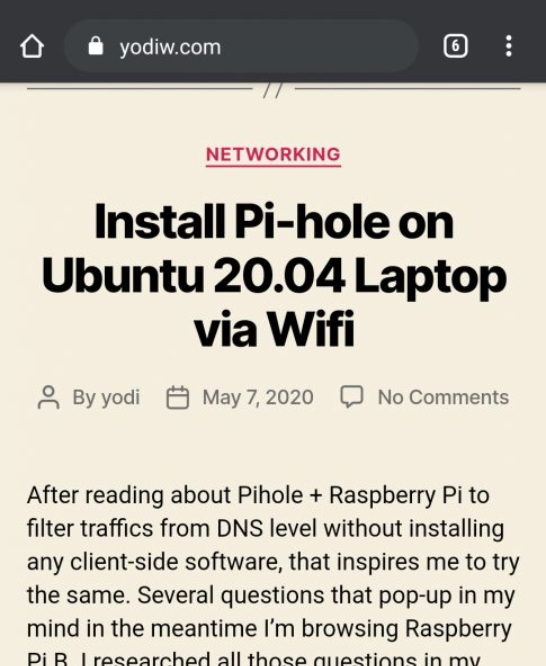

It’s done. Whenever you browse from your Android phone, you can see all the network traffic in Burp Suite. Happy hacking! To solve problem where Burp can’t monitor android app traffic because SSL pinning will be cover by next article.
4 replies on “Monitor Android network traffic with Burp”
Please share solution for SSL Pinning as well
Great job.
[…] I wrote the full tutorial and screenshot on how to do it at here: https://www.yodiw.com/monitor-android-network-traffic-with-burp/ […]
[…] I wrote the full tutorial and screenshot on how to do it at here: https://www.yodiw.com/monitor-android-network-traffic-with-burp/ […]